Camera Access⚓︎
Difficulty:
Objective⚓︎
Request
Gain access to Jack's camera. What's the third item on Jack's TODO list?
NanoSat-o-Matic
Hi there! I am a Ground station client vending machine. Apparently there is a huge need for NanoSat frameworks here, so they have put me in this room. Here, have a free sample!
Hints⚓︎
Hubris is a Virtue
From: Wombley Cube
In his hubris, Wombley revealed that he thinks you won't be able to access the satellite's "Supervisor Directory". There must be a good reason he mentioned that specifically, and a way to access it. He also said there's someone else masterminding the whole plot. There must be a way to discover who that is using the nanosat.
Solution⚓︎
Oh wow. The beginning of this challenge feels overwhelming. From the "NanoSat-o-Matic" vending machine we get a container running a "NanoSat MO Base Station Tool"; "GateXor" at the central console gives us a dedicated virtual Cubesat Simulator in the cloud, and config data for a Wireguard connection between container and Cubesat simulator. Must be Christmas!
Initial setup⚓︎
We extract the container from its archive and start it via the "build_and_run.sh" script. After some seconds, we connect using "vncviewer localhost:5900", reaching a Linux desktop running the fluxbox window manager.
GateXor gives us a Wireguard configuration; we start a Bash shell on the container and use vi to create /etc/wireguard/wg0.conf and insert the snippet for "your Wireguard configuration file" there.
[Interface] Address = 10.1.1.2/24 PrivateKey = dsBL1MAshH+5WUVxqMw25tAv6sJQHGhXgw2/RdbX9n0= ListenPort = 51820 [Peer] PublicKey = YQJ0ZC/rsmCiBWQh2m1J++mvyKzsnbEf3FtHVlEq8Wo= Endpoint = 35.193.220.99:51820 AllowedIPs = 10.1.1.1/32
Running
# wg-quick up wg0
Activating the Camera⚓︎
We launch the "nanoSat MO Base Station Tool" in the container's desktop (right mouse click on background -> Satellite Tools ->) "README.md" in the container's main directory instructs us to connect to a server via "maltcp://10.1.1.1:1024/nanosat-mo-supervisor-Directory". We put this into the field "Directory Service URI" and click "Fetch information". The left pane populates, and we click "Connect to the Selected Provider".
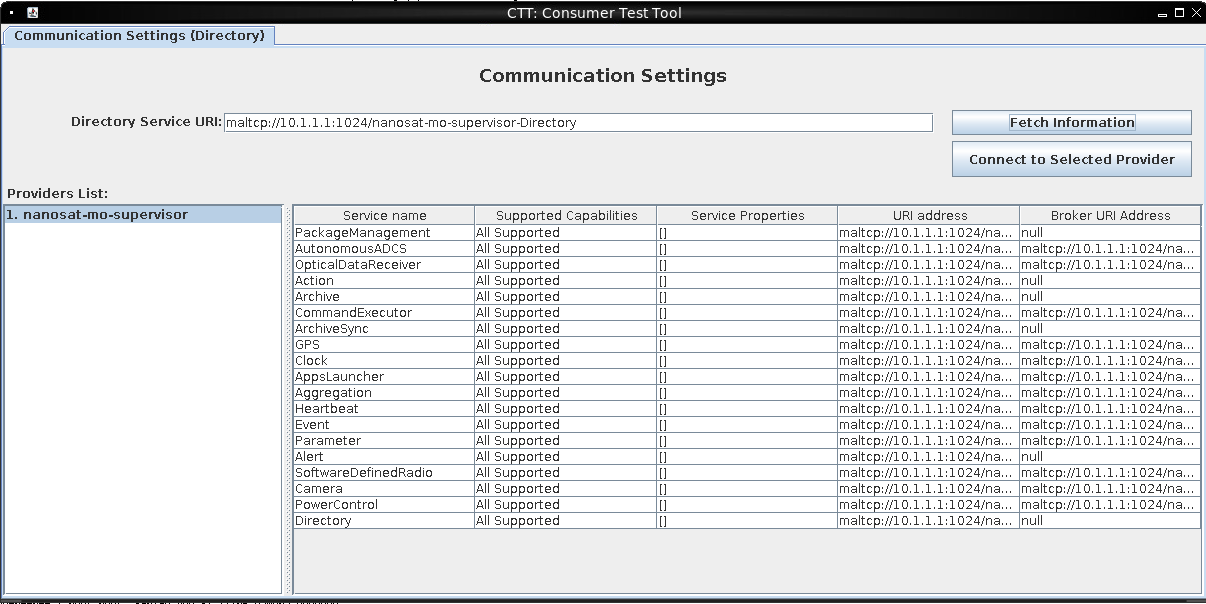
A new tab "nanosat-mo-supervisor" will open. There, we choose the "Apps Launcher service" card. As the "camera" app is not running, we select its line and click the "runApp" button at the bottom.
We return to the main tab "Communication Settings (Directory)". If "App: camera" is not yet visible in the "Providers List", we click "Fetch Information" again.
When "App: camera" is visible, we select it and click "Connect to Selected Provider"
In the card "Parameter service", we select the line having name "Base64SnapImage" and click the "enableGeneration" button at the bottom.
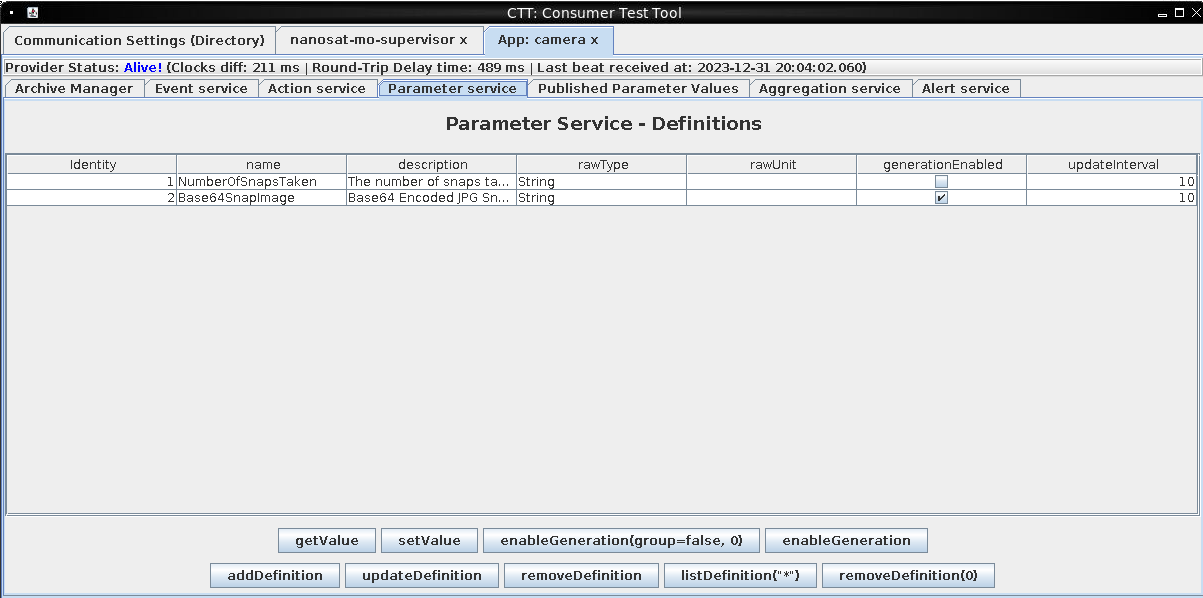
Every few seconds, a base64-encoded imgage is now transferred from the cubesat simulator to the container.
Activated the Camera
Capturing the Image with Wireshark⚓︎
As I am absolutely clueless of how to access the images from the Base Station Tool GUI, or where or if they are stored locally, we must take another path.
We will capture this data via wireshark and extract the image: Let's start wireshark via the fluxbox menu (Applications -> Networking -> Wireshark) and capture traffic on interface wg0 (this is the unencrypted side of the wireguard tunnel).
"tcp port 1025" is a good filter to limit the capture to camera traffic. All URIs of the "App: camera" provider start with "maltcp://10.1.1.1:1025", those of the "nanosat-mo-supervisor" use port 1024, so this filter helps exlude "noise".
We stop the capture after 10 seconds. Most of the packet contents in the middle of the capture will show the typical base64 pattern - the payload is blocks of characters from [0-9A-zA-Z+/]. We right-click one such packet and select "Follow -> TCP Stream".
A new window with the stream content opens; it might take some time time for wireshark to finish adding packets.
When wireshark has finished, we select not the "Entire conversation", but the direction "10.1.1.1:1025 -> 10.1.1.2:(some port)" using the selector button in the lower left corner.
"Save as..." now saves this to a file, e.g. "/root/camera.stream".
In a bash shell on the container, we use vim to edit "camera.stream". "vim" is well suited for such task, as it can handle binary data and long lines - in fact, the whole capture now is one single line.
The file should start like this:
1........a.HBy..M......5maltcp://10.1.1.1:1025/camera-ParameterInternal Broker!maltcp://10.1.1.2:1024/1995899082.^).....esa.NMF_SDK.NanoSat.SDK LIVE...esa..NMF_SDK..camera....SUB.....^).......'maltcp://10.1.1.1:1025 /camera-Parameter......Base64SnapImage..........................V...... .........../9j/4AAQSkZJRgABAQAAAQABAAD/2wBDAAUDBAQEAwUEBAQFBQUGBwwIBwcH Bw8LCwkMEQ8SEhEPERETFhwXExQaFRERGCEYGh0dHx8fExciJCIeJBweHx7/2wBDAQUFBQc
We remove everything up to but excluding /9j/ and save the file.
The result of base64-decoding it should be a JPEG image:
# base64 -d camera.stream > camera.jpg
# file camera.jpg
camera.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 2048x2048, components 3
We determine the name of the container and copy the image to our host machine:
$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
e5b66f08e3b3 nmf_client "/__cacert_entrypoin…" 3 hours ago Up 3 hours 0.0.0.0:5900->5900/tcp, :::5900->5900/tcp, 0.0.0.0:6901->6901/tcp, :::6901->6901/tcp boring_einstein
$ docker cp boring_einstein:/root/camera.jpg .
Got a camera image
We open "camera.jpg" and see, pictured in a silver sheen:
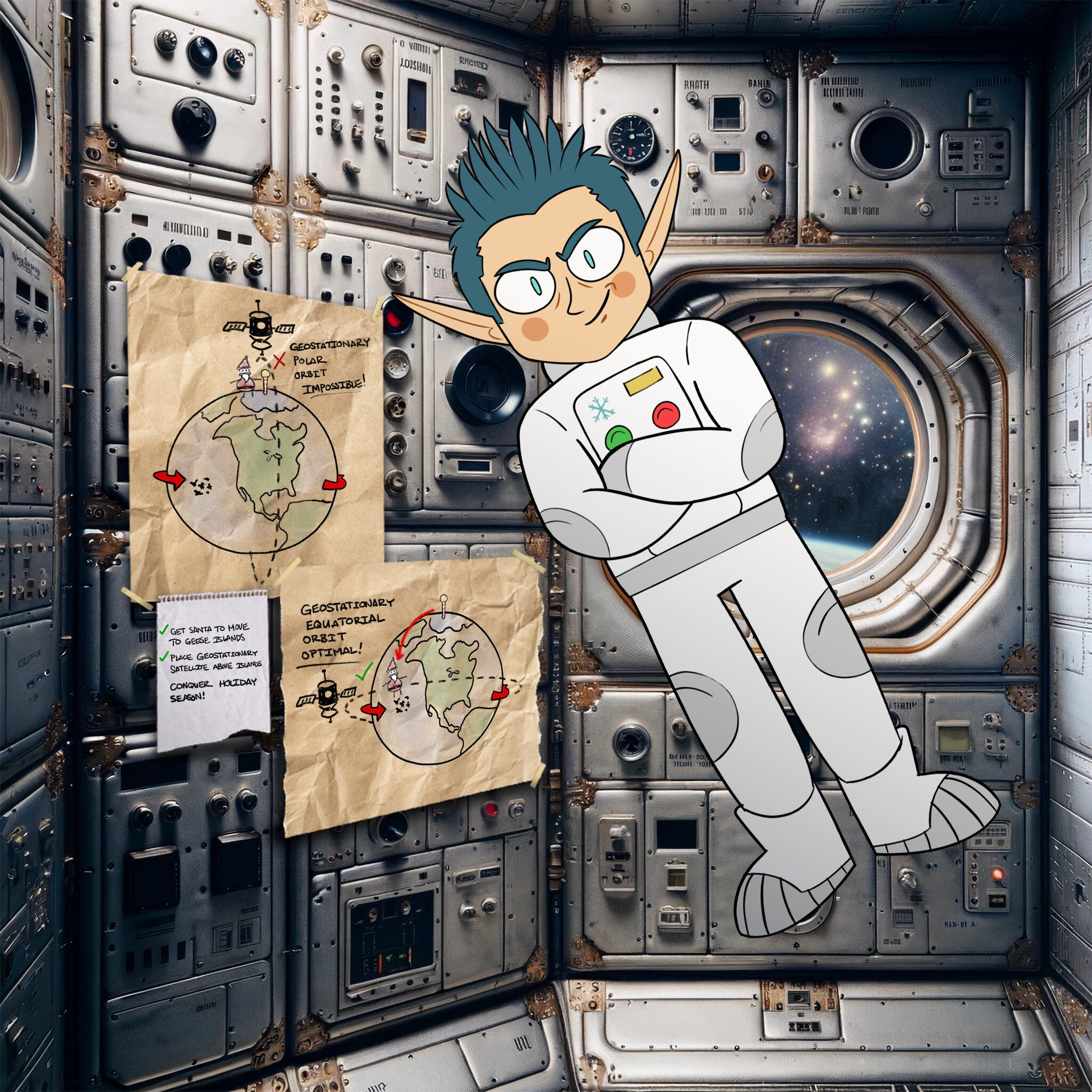 Jack Frost!
Jack Frost!
Jack has gained notoriety as the villain in HHC2021. Him being here again bodes not well.
Two diagrams explain that a geostationary satellite would not have worked over the north pole, but would indeed work here near the equator on Geese Islands.
Beside these we spot Jacks's todo list, with the solution to this challenge:
- GET SANTA TO GEESE ISLANDS
- PLACE GEOSTATIONARY SATELLITE ABOCE ISLANDS
- CONQUER HOLIDAY SEASON!
Found Jack's Todo List
Really snatch image from tcp stream?
I am unhappy with the solution of grabbing the image from the tcp stream. Should it not somehow be available in the GUI?
Answer
CONQUER HOLIDAY SEASON!
Response⚓︎
UNKNOWN PERSON
INSERT TEXT HERE